E-Books and White Papers
-

AOPG Insights-Is Malaysia Ready for GDPR
At the time of writing, we are barely a month away from the GDPR “going live” in the EU. Despite…
Read More » -

IT Modernisation in Malaysia – The Impact of Flash, HCI & Modern Computing
Technology is at the core of this transformation. The only way for businesses to evolve and embrace digitisation is to modernise…
Read More » -

DSA Micro Survey Indonesia – Transformation and Cyber Threat Commissioned by Trend Micro
The world of business and IT is in a state of massive transformation. Across South East Asia, businesses and governments…
Read More » -

DSA Micro Survey State of the Nation: The Singaporean Cyber Threat Commissioned by Trend Micro
Data is now acknowledged to be a company’s single most valuable business asset and in many cases, the business itself…
Read More » -

IBM Success Story with Rustan Commercial Corporation
When Pete Sison, Vice President for Information Technology, first joined Rustan Commercial Corporation (RCC) in 2015, he stated that one…
Read More » -

DSA Micro Survey Virtualisation and Cloud Strategy in ASEAN commissioned by Nutanix
Data & Storage Asean (DSA) conducted an online survey, commissioned by Nutanix, completed by 100 IT professionals from companies located…
Read More » -

Micro Survey Are Malaysians’ Data Enabling Their Business
Data & Storage Asean (DSA) has conducted a NetApp commissioned online survey, completed by 100 IT professionals from Malaysian-based companies to…
Read More » -

Everything A Small Business Needs To Know About Wireless Security
‘Wi-Fi’ which was trademarked by the Wi-Fi Alliance, which is the organization that owns the Wi-Fi registered trademark term, defines Wi-Fi…
Read More » -

Digital Transformation Starts With A Digital Workspace
The integrated mobile workspace solution is no longer an idea that the enterprise can overlook. It is a workspace solution…
Read More » -
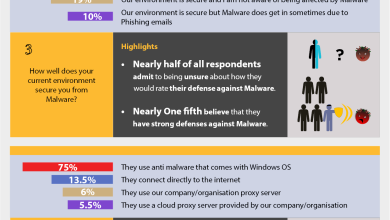
Micro Survey Advanced Cyber Security Threat Readiness in Malaysia
Cyber attacks are on the rise and the threats are changing every day. Malware, botnets, ransomware and other forms of…
Read More »

